At our payment platform, Webhooks provide a highly efficient method for receiving real-time notifications in your backend system. When specified events such as invoice generation, payment completion, deposits, and currency swaps occur, our system sends a notification via HTTP requests as a JSON payload.
Why Use Webhooks?
Real-Time Data Synchronization: Webhooks allow your backend systems to receive instant notifications of events, eliminating the need for periodic data polling, thereby significantly increasing efficiency and response speed.
Reduced Resource Consumption: Compared to traditional data polling methods, Webhooks are more efficient in data transmission and processing. Our system only sends data when events actually occur, reducing unnecessary network and computational resource usage.
Easy Integration and Use: Clients only set configuration once, after which notifications are automatically sent to a pre-configured URL whenever events occur. This simplifies the integration process, making it easier for partners and developers to access and utilize.
Supported Event Types
Our Webhook service supports a wide range of notification types, including but not limited to:
1.Invoice: Generation and status changes of invoices.
2.Payment: Payment initiation, approval, and completions.
3.Deposit: Confirmation of funds deposited.
4.Swap: Currency exchange operations.
Each Webhook notification includes all crucial data points related to the event, ensuring that you can take appropriate actions based on actual circumstances.
Webhook Signature
The security of our Webhook notifications is paramount, which is why each notification includes a signature in the header. This signature is calculated using HMAC_SHA256 to ensure the integrity and authenticity of the message.
The Signature Algorithm secures webhook notifications by encoding the JSON data using UTF-8, hashing it with HMAC-SHA256 along with a shared secret key, and then encoding the resulting hash in Base64 to produce a verifiable signature.
Example Header
hmac_signature: Fg5V5Oi20Zk59fPC52wPRNSxeOFVTKJvG75+7MzimjU=
Python Code Example
Here is an example of how you might implement this in Python:
import hmac
import hashlib
import base64
def generate_signature(data, secret_key):
# Create an HMAC-SHA256 object
hmac_obj = hmac.new(secret_key.encode(), data.encode(), hashlib.sha256)
# Compute the hash
hash_bytes = hmac_obj.digest()
# Encode the hash in Base64
signature_base64 = base64.b64encode(hash_bytes).decode()
return signature_base64
# Example usage
secret_key = 'your_secret_key'
data = '{"event": "payment_completed", "amount": 100}'
signature = generate_signature(data, secret_key)
print("Generated Signature:", signature)
Generating HMAC Signature
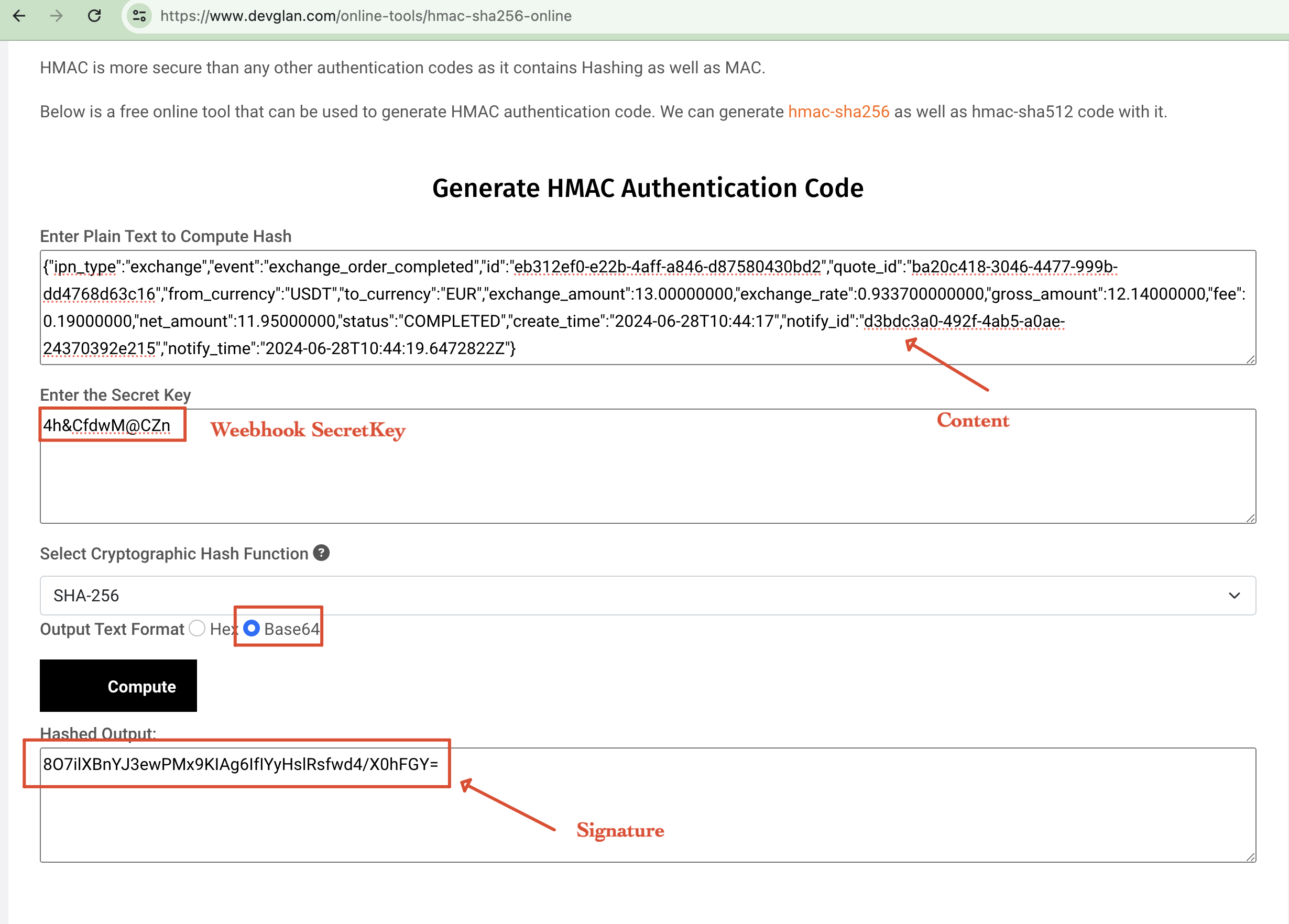
In this example, we demonstrate how to create a webhook signature using an online HMAC-SHA256 calculator. The process involves two main steps:
Content Extraction: Extract the JSON content from the webhook payload and service side signature from headers.
SecretKey Format
The key must be at least 8 characters long and include at least one letter, one digit, and one special character.
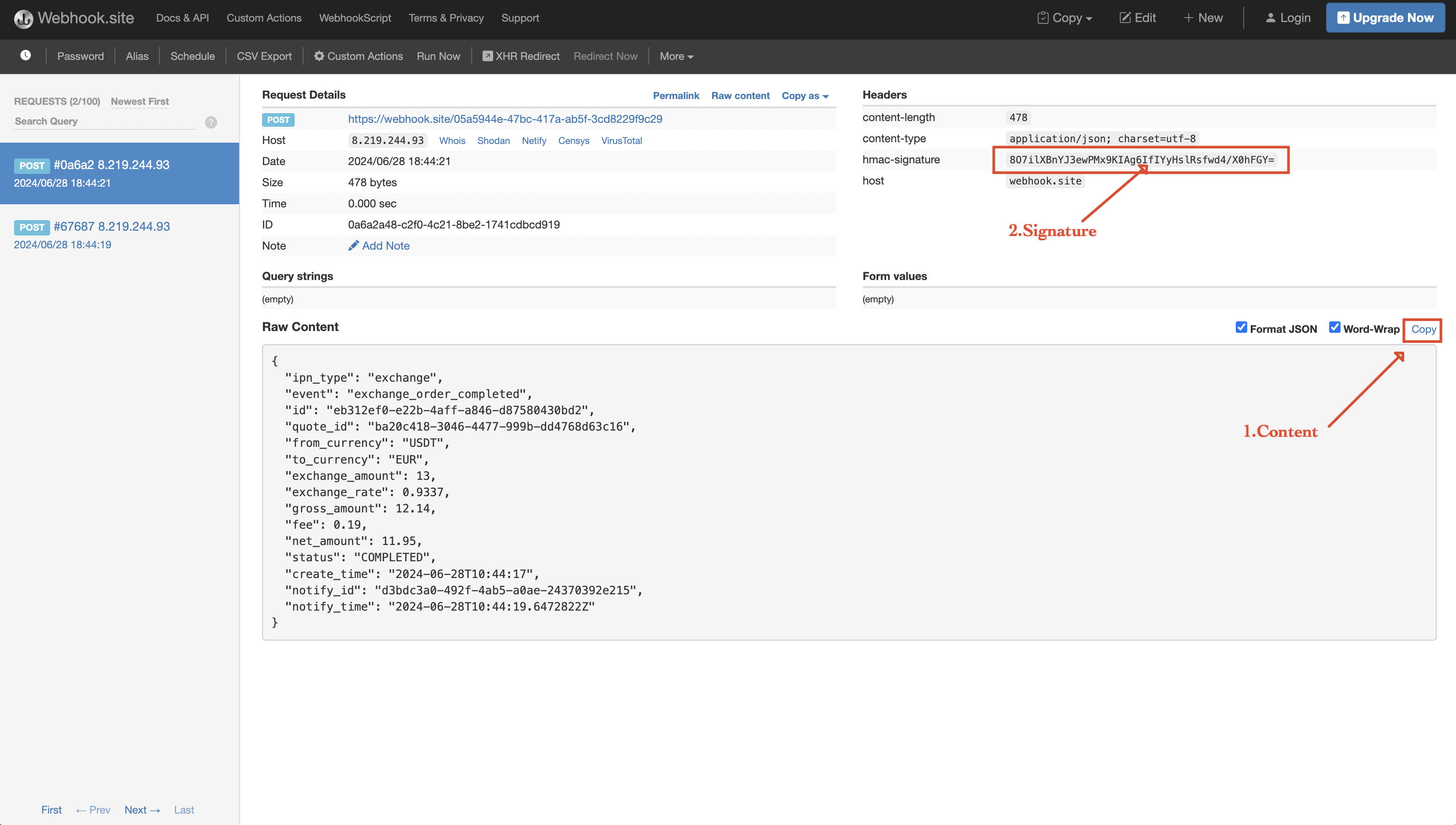
Signature Calculation: Use the extracted content and a secret key to generate an HMAC-SHA256 signature. An online tool like the one provided by devglan.com can be used for this purpose. By inputting the JSON content and the secret key into the tool, you can compute the HMAC authentication code. This computed code should match the signature provided in the webhook header.